A COM+ application is the primary unit of administration and security for Component Services and consists of a group of COM components that generally perform related functions. By creating logical groups of COM components as COM+ applications, you can take advantage of the following benefits of COM+:
A deployment scope for COM components.A common configuration scope for COM components, including security boundaries and queuing.Storage of component attributes not provided by the component developer (for example, transactions and synchronization).Component dynamic-link libraries (DLLs) loaded into processes (DLLHost.exe) on demand.Managed server processes to host components.Creation and management of threads used by components.Access to the context object for resource dispensers, allowing acquired resources to be automatically associated with the context.
Event ID 10006 & 1530, COM+ application not working
When a COM+ application stops working in Windows when a user logs off, you may see an error that resembles the following in the Application log on the client machine. If the client executable runs on the same computer as the COM+ server application, you will see this error on the COM+ server: You’ll also see events that resemble the following in the Application log of the computer on which the COM+ application runs:
What causes Event ID 10006 and 1530
According to Microsoft; DETAIL –1 user registry handles leaked from \Registry\User\S-1-5-21-1049297961-3057247634-349289542-1004_Classes:Process 2428 (\Device\HarddiskVolume1\Windows\System32\dllhost.exe) has opened key \REGISTRY\ USER \ S-1-5-21-1123456789-3057247634-349289542-1004_CLASSES The user identity that is associated with the COM+ application is logged on when the COM+ application is first initialized. So, this issue is triggered if this user were to log off of the machine then the user’s profile would get unloaded and the COM+ application can no longer read registry keys in the profile of the user identity. To resolve this issue, you’ll need to modify the default behavior of the User Profile Service via Group Policy Editor (gpedit.msc). Here’s how:
Launch Local Group Policy Editor.Navigate to the following path:
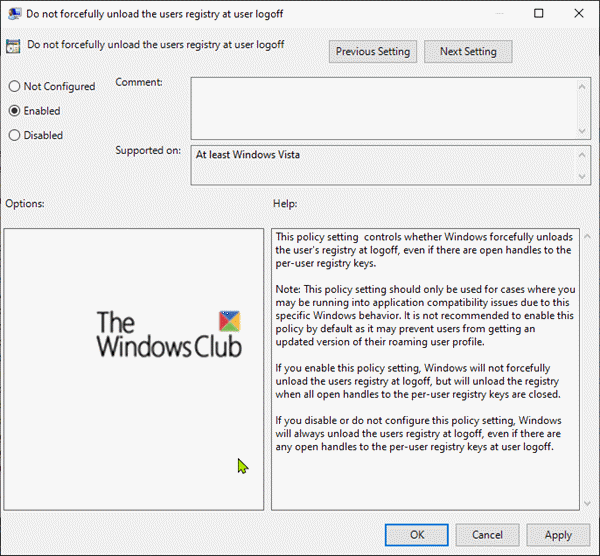
On the right pane, double-click the Do not forcefully unload the user registry at user logoff entry to edit it’s properties.Now change the setting from Not Configured to Enabled by selecting the corresponding radio button which disables the new User Profile Service feature.Click Apply > OK.
The policy-setting ‘Do not forcefully unload the user registry at user logoff‘ counters the default behavior of the Windows client operating system. When enabled, the User Profile Service will not forcefully unload the registry, instead, it waits until no other processes are using the user registry before it unloads it. Hope this helps!